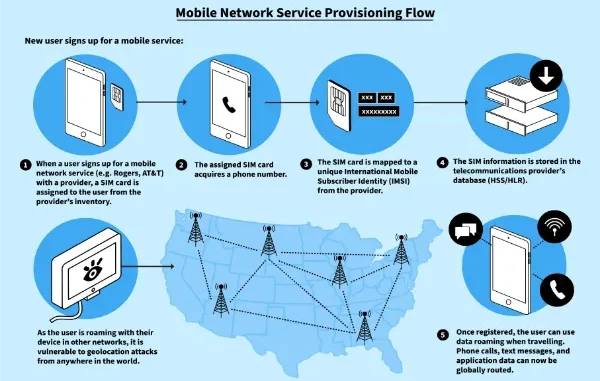
Mobile networks are the nerves of modern connectivity, though their signaling protocols have been and continue to be a favorite target for abuse. Faultfinders often misuse the Any Time Interrogation (ATI) query to surveil the whereabouts and extract privacy information of a subscriber, without any permission. The protection of these signaling pathways by 2026 is no longer an afterthought but has become a part of the critical quotidian operation.
This guide provides practical methods to detect and to block these unauthorized queries so that your network remains a place of high subscriber privacy and integrity.
Understanding ATI Queries and the Risk Landscape
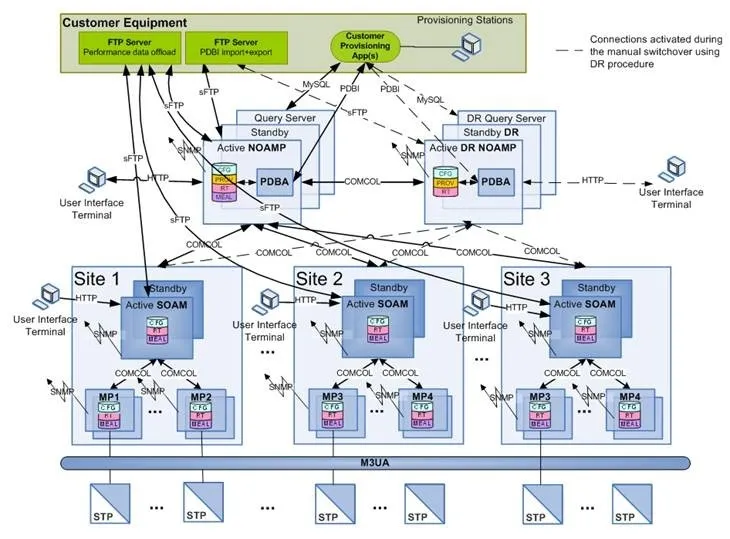
The ATI request is a conventional command in the MAP protocol. It is utilized by legitimate operators to interrogate the HLR for subscriber information, such as location or status, so that calls and SMS messages can be routed accurately.
But in a network like SS7 (Signaling System No. 7) that automatically trusts between operators, an attacker can take advantage of this role to break things. Unauthorised ATI queries make it possible for the user’s exact location to be identified or compromise a communication. That is incredibly dangerous, from a targeted spying perspective all the way to a mass data gathering operation.
Key Challenges in Filtering Signaling Traffic
Filtering such queries is not trivial. There are a few challenges for security teams in 2026:
- Camouflage of Legitimacy: Attackers obfuscate malicious queries to appear as operational traffic that can’t be blocked unilaterally.
- Increased Attack: SurfaceIntegrating cloud-native 5G cores with legacy 2G/3G networks results in intricate interconnects that are difficult to uniformly monitor.
- IoT Explosion: Billions upon billions of IoT devices flood the market, which increases signaling volume to generate “noise,” obfuscating low-volume, targeted attacks.
Best Practices for Filtering ATI Queries

If you really want to thwart unauthorized surveillance attempts, you’ve got to do more than simply rely on simple access control lists. A multi-layered approach is essential.
Deploy Application Level Gateways (ALGs)
Traditional firewalls may not have visibility to analyze signaling payloads. An Application Layer Gateway (ALG) works at Layer 7, hence it can perform Deep Packet Inspection. This allows for the system to verify the legitimacy of the message within the ATI query, and that it comes from a trusted source and is intended for a valid destination.
Enforce Strict Segmentation
This helps contain the case of a potential breach, and network segmentation restricts exposure. It is possible, however, that the important signaling elements, like the HLR, stay in areas to be designed separately. In State Wide Area network operations, for example, segmentation is used to ensure that a compromise at a regional branch location or in an outsourced partner network does not provide unmitigated access to the central subscriber database.
Implement Whitelisting and Geoblocking
Adopt a default-deny posture. Permit ATI requests only from contracted roaming partners. If you don’t have roaming arrangements with certain countries or operators, then start blocking all signaling traffic from these immediately.
Utilize Next-Generation Signaling Firewalls
Today’s signaling firewall is more than just a static rule list. They keep the status of the transactions and correlate ATI requests with recent location updates. In the case where a query message is received from a network towards which the subscriber is not roaming, the firewall identifies it as a deviation.
The Role of Modern Technologies
Combating sophisticated signaling attacks requires advanced tools that offer real-time visibility and automated response capabilities.
- Intelligence-Enabled Analytics: With machine learning algorithms, a baseline is established on the regular signalling traffic. They can find such small deviations, for example, that suddenly there are too many ATI queries on a particular high-value target.
- Threat intelligence integration): Integrate your signaling firewall with global threat intel feeds, allowing recognition of known parties that lease GTs to surveillance companies.
- SIEM Integration: Ingesting signaling logs into a Security Information and Event Management (SIEM) system enables the correlation of network events with other security alerts to gain a comprehensive perspective of the threat environment.
Impact of Signaling Threats: 2024-2025 Statistics
According to recent figures released by the European Union Agency for Cybersecurity (ENISA), telecoms security incidents are changing. Unless and until they can dramatically decrease the increasing number of incidents, industries are getting better at minimizing damage.
| Metric | Statistic (2024 vs 2023) | Insight |
| Total Reported Incidents | 188 (Increase of 20.5%) | Attack volume is growing, driven by automated tools. |
| User Hours Lost | 1,743 Million (Decrease of >50%) | Faster detection and response are reducing downtime. |
| System Failures | 60% of all incidents | Technical resilience remains the primary challenge. |
| Malicious Actions | 8% of all incidents | Targeted attacks persist despite being a smaller percentage. |
| Human Error | 19% of all incidents | Training and protocol adherence remain critical gaps. |
Conclusion
Unauthorized ATI requests are screened out, which is part of the subscriber privacy and network security. With strong ALGs, segmentation, and AI-driven analytics, operators can largely mitigate the risk of location tracking and fraud.
Security is not one time setup; it’s all about being vigilant and adapting. Regularly revisit your signaling firewall rules to outpace changing surveillance tactics.





Leave a Reply