
Cryptocurrency is often described as a technological breakthrough built on cryptography, decentralization, and autonomous digital contracts. These systems are designed to resist technical attacks and eliminate many of the weaknesses found in traditional finance. Yet despite this strong technological foundation, many of the most damaging losses in the crypto ecosystem have not come from code exploits. They have come from social engineering. Attackers manipulate people rather than systems, convincing users to hand over credentials, sign malicious approvals, or trust fraudulent platforms. In an environment where transactions cannot be reversed, this kind of deception can be devastating.
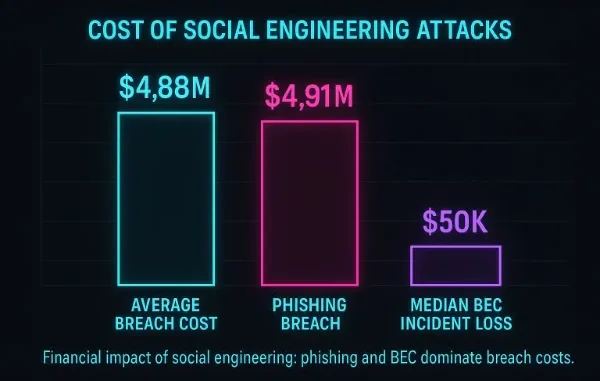
Social engineering refers to the psychological manipulation of individuals in order to gain unauthorized access to assets or information. In crypto it is particularly dangerous because anyone who obtains a private key, recovery phrase, or login credentials can immediately access and transfer funds. There is no authority that can undo the damage. A single successful attack can lead to a total loss of assets. In fact, losses caused by human manipulation often exceed those caused by technical vulnerabilities.
Why Social Engineering Thrives in the Crypto Environment
Cryptocurrency users operate without the extensive safety nets that exist in traditional banking. A bank can freeze an account, reverse a transfer, or flag a suspicious transaction. None of these protections exist on decentralized networks. Blockchain transactions are final, and wallet ownership depends entirely on who controls the private keys associated with the funds.
Because self custody places full security responsibility on users, attackers focus on tricking individuals rather than attempting to break encryption. A criminal only needs one mistake. Users must protect their wallets, manage recovery phrases, and verify every action they take on unfamiliar platforms. While this level of autonomy is empowering, it also creates fertile ground for social engineering.
The crypto ecosystem also includes a broad mix of users. Some have deep technical knowledge while many others are newcomers inspired by media coverage or investment trends. Those newer to the space are often unaware of common attack patterns. Criminals exploit this knowledge gap continuously.
Phishing and Imitation Scams
Phishing remains the most widespread form of social engineering in crypto. Attackers create fake versions of exchange portals, wallet dashboards, and transaction interfaces. These fraudulent sites often mirror the design of legitimate services so closely that even experienced users may fail to notice the differences. Once a victim enters credentials or recovery phrases, attackers seize the wallet.
A common variation of this tactic is the fake support message. Attackers pose as customer service agents or community moderators and send direct messages to users who have expressed confusion on public forums. The impersonator appears helpful and professional, guiding the user through supposed troubleshooting steps that are actually designed to collect sensitive information.
This tactic has driven significant losses. In 2025, federal reports documented more than two hundred sixty two million dollars stolen in account takeover schemes across financial and investment platforms. Criminals persuaded users to reveal authentication codes or sign into counterfeit login portals. Once access was obtained, attackers moved the stolen funds into cryptocurrency to evade recovery efforts. The combination of impersonation and irreversible transactions made these losses exceptionally difficult to trace.
Fake Applications and Wallet Drainers
Deceptive software is another powerful tool for social engineers. Attackers publish counterfeit wallet apps and browser extensions that appear legitimate. When users install these applications, the software captures recovery phrases, monitors transactions, or injects malicious prompts.
Wallet drainers operate by presenting connection screens that request broad permissions. A user may believe they are approving a simple transfer, but the permission actually grants the attacker full control over the wallet’s assets. Once approval is given, funds disappear almost instantly.
These operations are highly organized. Cybercriminal groups deploy thousands of automated phishing pages and distribute fake apps through channels that mimic official release announcements. Some even maintain multilingual scripts and fake support teams to assist in the deception.
Impersonation and Deepfake Manipulation
Advances in artificial intelligence have transformed social engineering. Attackers can now generate realistic voice clips and video messages that imitate trusted individuals. This capability has expanded the reach of impersonation attacks.
Corporate employees responsible for treasury wallets have been targeted with audio messages that sound identical to their executives. These messages instruct them to authorize urgent transfers or participate in confidential transactions. When crypto is involved, attackers take advantage of the speed and finality of blockchain transfers to complete the theft before anyone realizes the request was fraudulent.
Deepfake manipulation has also begun appearing in peer-to-peer trading. Criminals impersonate respected community members, urging users to test new tools or connect wallets to preview platforms. The moment the wallet connects, the attacker drains the assets.
Rug Pulls and Confidence Games
Social engineering does not always focus on individuals. Entire communities can be manipulated through confidence schemes. Rug pulls occur when fraudsters launch a seemingly promising crypto project, build enthusiasm, and encourage users to deposit funds or buy tokens. Once interest peaks, the creators vanish with the assets.
The psychology behind these schemes is central to their success. Attackers cultivate a sense of excitement, urgency, and exclusivity. They use social proof by generating positive chatter, posting fabricated testimonials, or orchestrating influencer endorsements. Many victims later admit that early warnings were overlooked because group momentum drowned out caution. Crypto’s culture of rapid participation and fear of missing out amplifies the effectiveness of these confidence games.
Exchange Related Scams and Real World Case Study
Even major exchanges with strong technical cybersecurity have suffered losses through social engineering. In 2025, coordinated phishing campaigns targeted users of several large trading platforms during periods of high transaction activity. Attackers distributed fraudulent links that looked identical to official login portals. Users who entered their credentials inadvertently handed attackers full access.
Once inside the accounts, criminals initiated withdrawals and routed assets through privacy oriented tokens or mixers to obscure their trail. In some cases exchanges detected suspicious activity quickly, but the irreversible nature of crypto transactions meant that funds were often lost before security teams could act.
This case demonstrates that even the most sophisticated infrastructure cannot protect users who are deceived into revealing their credentials.
Social Engineering in DeFi and Smart Contract Ecosystems
Decentralized finance expands the attack surface dramatically. Scammers routinely replicate the branding and layout of real DeFi platforms. They release imitation versions that appear nearly identical to legitimate interfaces. Users who interact with these clones may unknowingly grant spending permissions that allow attackers to drain tokens at will.
Since DeFi involves approval mechanisms that authorize contracts to move funds, attackers exploit this feature by disguising malicious requests as routine operations. These approvals remain active until manually revoked, which many users do not realize. This makes DeFi an attractive target for social engineering that blends psychological manipulation with permission based exploitation.
Conclusion
Social engineering remains one of the most powerful threats in the cryptocurrency ecosystem. The technology behind blockchain may be secure, but human behavior is not. Criminals understand this and dedicate substantial effort to influencing people rather than breaking systems.
High profile incidents, from large scale account takeovers to sophisticated impersonation attacks, demonstrate that human centered vulnerabilities can lead to substantial financial loss. Protecting crypto assets requires equal attention to psychological defenses and technical safeguards.
The future of crypto security depends on building informed communities, designing platforms that anticipate user mistakes, and promoting secure habits across all levels of experience. When people understand the tactics used against them and adopt thoughtful practices, the effectiveness of social engineering diminishes. With stronger awareness and improved security culture, the crypto ecosystem can better protect itself against the human element that attackers continue to exploit.





Leave a Reply